In today's fast-paced world, businesses require efficient and secure payment processing systems to meet the demands of their customers.The Point of Sale (POS) terminal has transformed the way transactions are conducted, revolutionizing the payment process. Whether you're a small retail store or a large restaurant chain, understanding the capabilities and benefits of a POS terminal is essential for running a successful business. In this blog post, we will delve into what a POS terminal is, how it works, and the advantages it offers to businesses and customers alike.
What is a POS Terminal?
A POS terminal, referred to as a cash register or checkout terminal, is a combined hardware and software system utilized for transaction processing at the point of sale. It functions as a central hub where customers complete payments for goods or services, while businesses capture and monitor sales data. Unlike traditional cash registers, modern POS terminals are equipped with advanced features that streamline and enhance the entire payment process.

How Does a POS Terminal Work?
A typical POS terminal consists of several components working together to facilitate seamless transactions. These components include:
Hardware: A typical POS terminal comprises hardware components such as a touchscreen display, barcode scanner, cash drawer, receipt printer, and optionally, a customer-facing display. Advanced models may incorporate additional features such as built-in card readers or biometric authentication systems.
Software: The software running on a POS terminal is specifically designed to handle various functions such as processing payments, managing inventory, generating reports, and integrating with other business systems. The software interface is designed to be intuitive, user-friendly, and customizable, catering to the unique requirements of various businesses.
Payment Processing: Perhaps the most critical function of a POS terminal is processing payments. It provides support for a wide range of payment methods, including credit and debit cards, mobile payments, as well as contactless options like NFC (Near Field Communication) or QR code scanning. The terminal securely captures transaction data, encrypts it, and communicates with the payment gateway to authorize and complete the transaction.
Benefits of POS Terminals
Enhanced Efficiency: POS terminals optimize the checkout process, minimizing wait times and enhancing customer satisfaction. By incorporating functionalities such as barcode scanning and integrated inventory management, businesses can efficiently handle transactions and instantly update stock levels, resulting in streamlined operations and improved customer experience.
Accurate Sales Tracking: POS terminals provide businesses with accurate and detailed sales data. This data aids in analyzing customer purchasing trends, identifying popular products, and making well-informed decisions regarding pricing, promotions, and inventory management.
Inventory Management: Numerous POS systems provide inventory management capabilities that empower businesses to monitor stock levels, establish automatic reorder points, and generate reports on product performance. These features help prevent stockouts, reduce waste, and optimize inventory turnover for enhanced operational efficiency.
Simplified Accounting: POS terminals automatically generate comprehensive sales reports, eliminating the necessity for manual calculations and data entry. This simplifies accounting processes, reduces the chances of human error, and saves valuable time during financial reconciliations.
Enhanced Security: POS terminals employ robust security measures to protect sensitive customer data and prevent fraudulent activities from occurring. By employing encryption technologies, tokenization, and adhering to Payment Card Industry Data Security Standards (PCI DSS), they ensure secure transactions and instill trust in customers.
How to ensure that a POS terminal is compliant with security standards?
Ensuring that POS terminals are compliant with security standards is crucial for businesses to protect sensitive customer data and prevent potential security breaches. Here are some key practices to follow:
Opt for Solutions That Meet PCI-DSS Compliance: PCI-DSS (Payment Card Industry Data Security Standard) compliance comprises a set of security standards created by major card brands to protect cardholder data. When selecting a POS terminal, ensure that it meets the PCI-DSS requirements. Ensure that the terminals you choose are certified and validated by the PCI Security Standards Council.
Keep Software Up-to-Date: Ensure Regular Software Updates for POS Terminals: It is crucial to regularly update the software running on your POS terminals. These updates usually encompass security patches and bug fixes that specifically target vulnerabilities and enhance the overall security of the system. Establish a process to monitor and install updates promptly to ensure that your terminals are protected with the latest security measures.
Use Strong Passwords: Enforce Secure Password Policies for POS Terminal Administration: Implement strong password policies when accessing the administrative functions of your POS terminal. Employ strong passwords that incorporate a mixture of uppercase and lowercase letters, numbers, and special characters. Avoid using default or easily guessable passwords, and enforce regular password changes to bolster security measures.
Secure Network Connections: Guarantee secure network connections for POS terminals to safeguard data transmission. Use secure protocols such as Wi-Fi Protected Access (WPA2) for wireless connections and Virtual Private Networks (VPNs) for remote access. Regularly monitor network traffic and employ firewalls to protect against unauthorized access.
Encrypt Data: Enable data encryption on your POS terminals. Encryption converts sensitive data, such as credit card information, into unreadable code, making it difficult for unauthorized individuals to access or decipher. Implement end-to-end encryption to secure data from the moment it is captured at the terminal until it reaches the payment processor.
Implement Access Controls: Control access to the POS terminal by assigning unique user accounts and granting appropriate permissions based on job roles. Restrict Administrative Access to Authorized Personnel: Limit access to administrative functions of the POS terminal to authorized personnel only. Regularly review and update user accounts to ensure that access privileges are accurate and up to date, thereby maintaining strict control over who can access critical system settings and configurations.
Train Employees on Security Best Practices: Educate employees on security best practices related to POS terminals. Train them on identifying and reporting potential security threats, recognizing phishing attempts, and following proper handling procedures for sensitive data.
Conduct Regular Security Assessments: Conduct Regular Security Assessments and Audits for POS Terminals: Implement routine security assessments and audits for your POS terminals, which may involve vulnerability scanning, penetration testing, and compliance audits. These proactive measures help identify system weaknesses or vulnerabilities, enabling timely remediation and ensuring a robust security posture.
Monitor and Detect Anomalies: Implement systems to monitor and detect anomalies or suspicious activities related to your POS terminals. Set up intrusion detection systems, log file monitoring, and real-time alerts for any unusual behavior. Promptly investigate and respond to any security incidents or breaches.
By implementing these practices, businesses can greatly enhance the security of their POS terminals and effectively mitigate the risk of data breaches. It's important to stay updated on the latest security standards, industry best practices, and emerging threats to ensure ongoing compliance and protection of customer information.
What vulnerabilities should businesses be aware of POS terminals?
When it comes to POS terminals, businesses should be aware of several common vulnerabilities that could potentially compromise the security of their systems. Here are some key vulnerabilities to consider:
Weak Passwords: The use of weak or easily guessable passwords is a significant vulnerability. Default or common passwords make it easier for unauthorized individuals to gain access to the POS terminal's administrative functions and sensitive data.Businesses should establish and enforce robust password policies, promoting the use of strong passwords and encouraging regular password changes.
Outdated Software: Running outdated software on POS terminals exposes them to known security vulnerabilities, which hackers frequently exploit to gain unauthorized access or install malicious software. It is crucial to keep the software up to date to minimize such risks. Regularly updating and patching the software on POS terminals is critical to address any security flaws and protect against potential attacks.
Lack of Encryption: Neglecting to encrypt sensitive data, such as credit card information, during transmission and storage poses a significant vulnerability that can be exploited by malicious actors. It is imperative to implement encryption measures to protect such sensitive data effectively. Without encryption, intercepted data can be easily accessed and misused. Implementing end-to-end encryption is essential to ensure the protection of data throughout the entire payment process.
Unsecured Network Connections: Weak or unsecured network connections expose POS terminals to potential attacks. If wireless networks are used, businesses should ensure they are protected with strong encryption and proper access controls. Neglecting to secure network connections can lead to unauthorized access or interception of data, posing significant security risks.
Malware and Malicious Software: POS terminals are susceptible to malware and other malicious software. Malware can be introduced through various means, including infected USB drives, phishing attacks, or compromised network connections. Businesses should implement robust antivirus and anti-malware solutions on their POS terminals and regularly update them to detect and prevent such threats.
Insider Threats:Internal employees who have authorized access to POS terminals can potentially pose a security risk. Insider threats may involve intentional or unintentional actions that compromise system security. Implementing access controls, user permissions, and regular employee training on security best practices can help mitigate this risk.
Lack of Security Monitoring: Failing to monitor POS terminals for suspicious activities or anomalies leaves businesses unaware of potential security breaches. Implementing security monitoring systems, such as intrusion detection and log file monitoring, enables prompt identification and response to security incidents.
Physical Security: Neglecting physical security measures for POS terminals can lead to unauthorized access or tampering. Businesses should ensure that terminals are physically secured, such as being placed in a locked area or using security cables to prevent theft or tampering.
Lack of Employee Training: Insufficient employee awareness and training on security best practices can leave businesses vulnerable. Employees should be educated on identifying phishing attempts, handling sensitive data, and following proper security protocols to minimize the risk of human error or unintentional security breaches.
Third-Party Vulnerabilities: POS terminals often rely on third-party software or services, such as payment processors or software integrations. Businesses should ensure that these third parties adhere to strict security practices and regularly update their systems to protect against vulnerabilities that could impact the overall security of the POS terminals.
By understanding and addressing these common vulnerabilities, businesses can take proactive measures to enhance the security of their POS terminals and protect sensitive customer data from potential threats. Regular security assessments, ongoing training, and staying informed about emerging vulnerabilities and attack vectors are crucial for maintaining a secure payment environment.
Are there any recommended POS terminals for businesses?
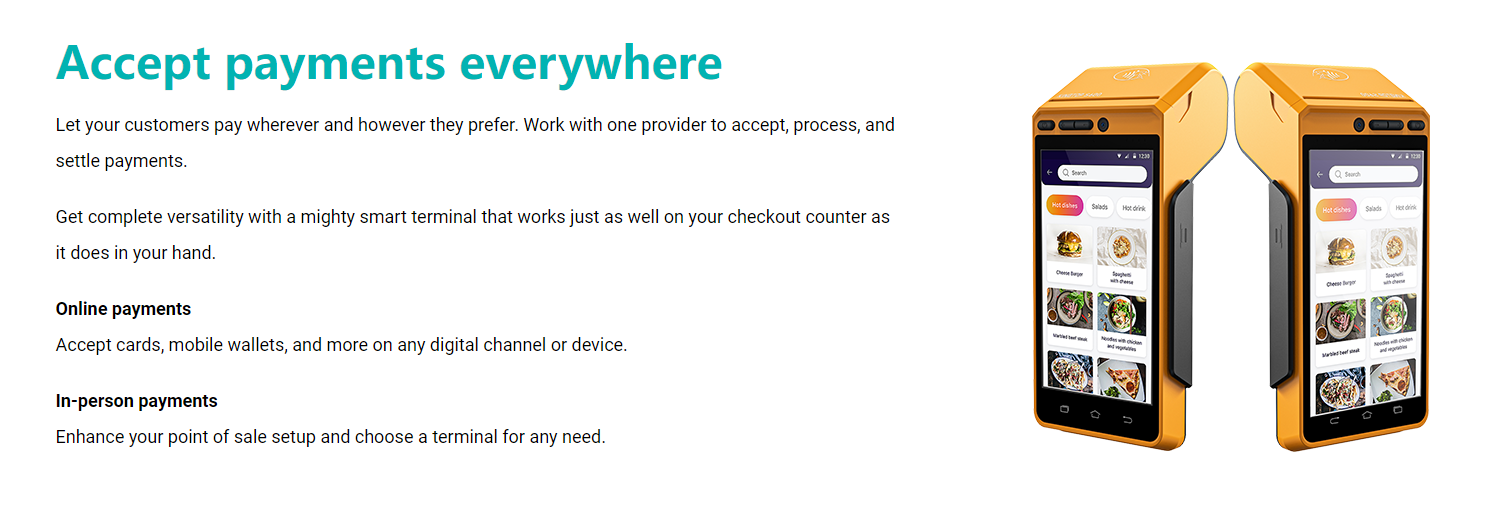
KingTop, as a provider of POS terminals, offer you KT-S600. The KT-S600 POS terminal is a convenient payment solution that enables businesses to accept payments anywhere, providing flexibility and convenience. Equipped with a built-in POS receipt printer that uses 58*35mm printing paper, the device eliminates the need for print cartridges or ribbons. This not only reduces operating costs but also guarantees quiet operation and enables high-speed printing capabilities. The terminal supports multiple payment methods, including magnetic stripe cards, IC cards, contactless cards, and QR code payments, offering customers a wide range of options.
When it comes to connectivity, the KT-S600 offers advanced options such as 4G, 3G, 2G, Wi-Fi, Bluetooth, and GPS positioning. With support for both Bluetooth printer mode and ESC/POS mode, the device ensures seamless integration with other devices, enhancing its versatility and compatibility. Powered by a premium quality 3100mAh 7.6V Li-ion battery, it allows for fast charging and extended usage time, making it ideal for prolonged working periods.
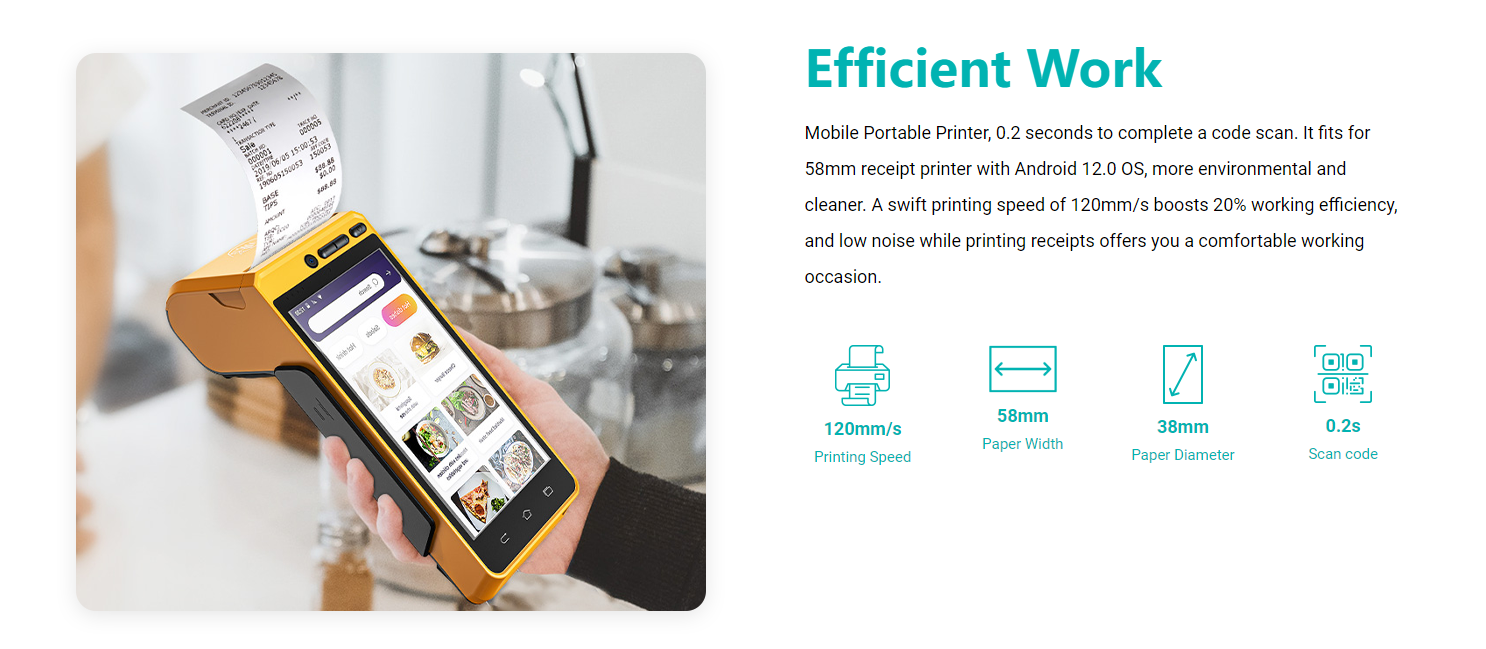
The KT-S600 is an Android POS terminal receipt printer that comes preloaded with catering and store management apps, providing convenient and ready-to-use solutions for businesses in the food and retail industries. It also provides free SDK support, enabling businesses to develop their own custom Android software tailored to their specific needs. The device is designed to be mobile and portable, with a swift 0.2-second code scanning capability. Operating on the Android 12.0 OS, it promotes environmental friendliness and cleanliness.

With an impressive printing speed of 120mm/s, the KT-S600 enhances working efficiency by 20% compared to traditional printers. Furthermore, the KT-S600 operates quietly, ensuring a comfortable working environment for businesses. By combining all these features, the KT-S600 provides a comprehensive and efficient solution for businesses' payment and printing needs.
As technology continues to advance, POS terminals have become an integral part of modern business operations. Their ability to streamline transactions, provide accurate sales data, and enhance efficiency has revolutionized the way businesses interact with customers. POS terminals empower businesses to deliver exceptional customer experiences and optimize their operations through features such as multiple payment options, efficient inventory management, and robust security measures. By embracing this technology, businesses can stay ahead in today's competitive marketplace and meet the evolving needs of their customers.











